We don’t need SMS 2FA.
I’m going to break down why we don’t need SMS 2FA and give you a replacement that is not only better but cheaper and easier too.
What Is SMS 2FA?
Hopefully, if you’re reading this, you have a good understanding of SMS 2FA.
If you don’t, SMS 2FA is the text message you get after entering your username and password. It’s another factor that is needed to log into an account.
What’s The Purpose Of SMS 2FA?
The goal of any 2FA is if your first factor (your password) is already known, the second factor (SMS 2FA) will keep the attacker out.
What are the ways a password is already known?
- Phishing.
- Password reuse/credential stuffing attacks.
- Malware.
- Guessing/brute force.
These are the most common ways a password is already known and why we use SMS 2FA.
Now the question becomes, does SMS 2FA actually solve these attacks? Not only that but is it the best option?
1. Why SMS 2FA Is Not Immune To Phishing
Phishing is when you get someone to go to the wrong website that looks like the real website and get them to enter their credentials.
Sounds simple enough; the user would fall for entering their username and password, but since the SMS 2FA code is one time use the attacker knowing it will be useless to them.
The problem is that this assumes hackers don’t evolve and change strategies. It’s not 2004 anymore; phishing has progressed quite a lot.
One Example Is Modlishka
To understand how this attack works, you need to think of the website the attacker sent you to as a web browser.
Your web browser goes to the attacker’s website. The attacker’s website then acts as a web browser for your web browser.
The user is using the real website but through the lens of the attacker’s website. Besides the URL in the user’s web browser not being correct, they’re none the wiser.
The user logs in with 2FA, and the attacker now has a session cookie, which keeps them logged in. The attacker has the username, password, and 2FA code.
The attacker’s server (aka “web browser”) has the session which means they’re already logged in and can do whatever they want. They could even turn 2FA off since most services don’t require 2FA to turn 2FA off once logged in.
Modlishka Isn’t The Only One
Since Modlishka is open source and free you get many variations that are also open source and free. Here is another example…
This threat not only affects websites but also online password manager too. Here is a video of a password manager getting phished and all the password stolen. This is a good reason why I pepper my important passwords.
These phishing attacks have set the new floor for phishing. It only can get worse from here as the attackers will not go back to worse phishing programs.
This is why SMS 2FA is not a solution to the phishing problem.
The replacement at the end can help stop phishing.
2. SMS 2FA Doesn’t Stop Credential Stuffing Attacks
Saying SMS 2FA doesn’t stop credential stuffing attacks seems to be a sticking point for some.
The problem comes from the misunderstanding of credential stuffing attacks.
Jarrod Overson answers it best…
I suggest you read the rest of what Jarrod wrote.
Attacks are layered and seeing an SMS 2FA screen doesn’t mean the attacker calls it quits. Instead, that user’s username and password go on a new list for the next round of attacks. The more the users are filtered, the more valuable they become as the attacker gets closer to their goal.
You haven’t made it more difficult for the attacker; you instead made the user more valuable to the attacker.
The next attack could be a targeted phishing attack, and as we know, SMS 2FA doesn’t hold up to that. What’s scarier is that a lot of users don’t have any 2FA on their email and love to reuse passwords especially ones that the attacker already filtered out from the credential stuffing attack. This means the attacker is just one password reset away from getting to their target after taking over the email account. 2FA is not as popular and abundant as everyone in the tech community thinks; 90% of Gmail users don’t use any 2FA.
This is why we say SMS 2FA is only “kicking the can down the road“. You’re not solving the problem but only delaying it.
The replacement at the end makes credential stuffing attacks useless.
3. SMS 2FA Doesn’t Stop Malware
The first immutable law of security.
SMS 2FA doesn’t protect the user against malware. There exist malware today that has shown that 2FA can’t stop it.
Even better, if the malware has control over the device, they can change any web address to point to any website and perform the Modlishka attack.
Malware is a lose-lose situation.
4. Guessing And Brute Force Attacks
Straight up guessing someone’s password is not easy. Math and time are against you.
Unless the user is reusing the same or similar password, guessing is not something that happens much.
Example Of How Hard It Is To Guess A Password
Guessing passwords is not easy; here is an example with me telling you the password requirements.
Length = 16 exactly
Character set = 62 (upper, lowers, numbers)
If its precisely 16 characters long, it would take 1,487,111,351 years to guess all possibilities at 1 trillion guesses per second.
This is ignoring slow hashing algorithms that would significantly extend guess time.
Most Services Already Stop Guessing Attacks
This is especially true on many services as they limit such attacks from happening in the first place.
It’s not hard to see one username being hit a lot of times with wrong password guesses.
Even if it’s from multiple IP addresses, you can still lock the user’s account as many services already do.
SMS 2FA Resets
Before we get to the replacement, we need to talk about SMS Resets.
And yes, I hear many of you right now saying SMS 2FA is not SMS Resets.
While this is true, it would be disingenuous to not talk about it because SMS Reset often comes along with SMS 2FA. They’re apart of the package on many websites, whether you want them or not.
We can’t ignore SMS Resets because this often means you can bypass everything with just a phone number and get into an account. Even worse are the websites that don’t have SMS Resets but add it later because they already have SMS 2FA.
SMS Resets are the worst thing about SMS 2FA, and ignoring it “because they’re not the same” is not helping the situation.
The Replacement – Do This Instead Of SMS 2FA
What’s great about the replacement to SMS 2FA is that it’s easier, cheaper, and more effective.
It’s quite shocking that we’re not doing it more often…
Generate the passwords for the users!
It’s that simple. I’ve already done a massive write up on why websites should generate passwords for users here.
It solves all the shortcomings of SMS 2FA. It’s easier to understand. It’s easier to implement. It’s cheaper and no need to use 3rd party support.
Educating Users Happens At Signup
Besides dorks like me, the average user is not going to research passwords and how to be more secure.
The place where users are getting educated about passwords is happening at the signup page.
We’ve spent years teaching users to make complex passwords with password requirements when we should have been teaching them to use unique passwords.
The best way to teach a user to use a unique password is to do it for them. Creating passwords for users gets them to think of passwords as something you store, not something you remember.
Passwords Need To Be Stored, Not Remembered
Generating passwords for users gets them to treat passwords like they do phone numbers. No one remembers phone numbers anymore as they use the contact app on their phone or little black book.
Instead of giving password requirements, tell the user to write the password down, let the browser store it, or use a password manager.
Many users are simply not aware of such things and need to be told.
It’s Not 2004 Anymore
You can’t use the internet without a web browser and every web browser offers to store and fill passwords for you.
Every browser has profiles that allow you to log in from any computer and get passwords and bookmarks.
Every major browser works on all devices, even mobile.
It’s so easy that users have to go out of their way not to use the password storage features in their web browser.
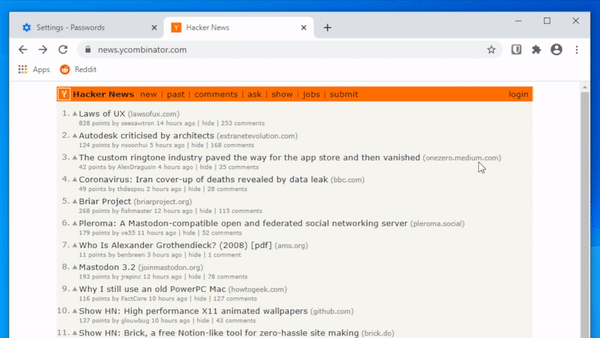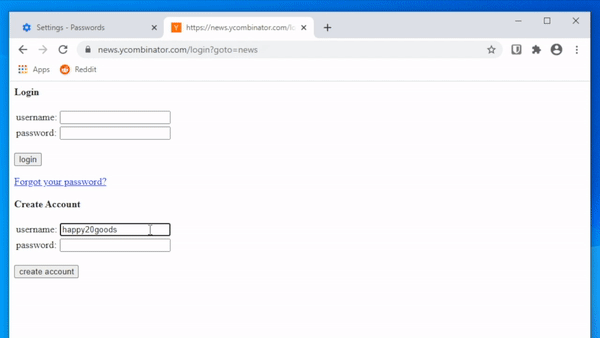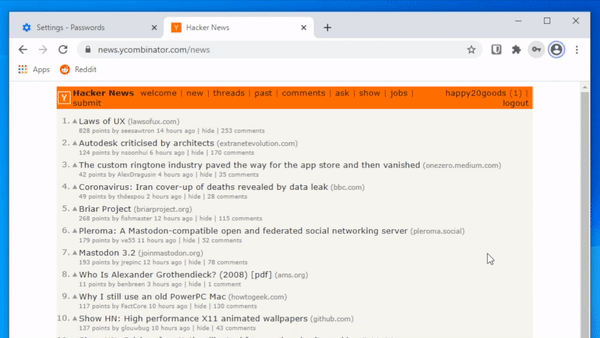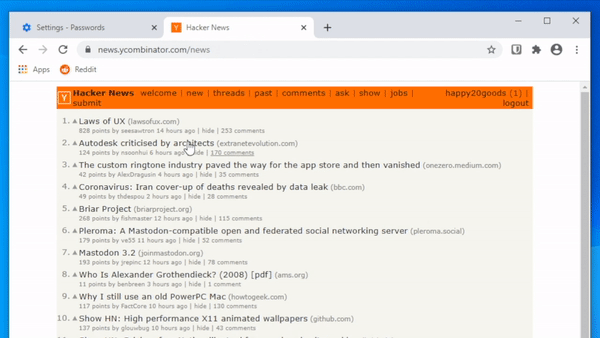
If they don’t trust the web browser, they can still use paper and pencil. It’s okay to write down your passwords, we’ve been saying it for over a decade.
The best part is that the password doesn’t need to be long or complex if the service does proper peppering. We can shift a lot of the burden away from the user while making them more secure.
This Works For Everyone
It doesn’t matter how much money you have or how smart you are, generating passwords works for everyone.
SMS 2FA requires a user to have a working phone and a working phone number. Generating passwords requires a user to have a pen and paper.
Phone numbers can be abused for tracking and advertising while pen and paper can not.
People understand keeping secrets, even ones they do not create.
People have no issues with storing secrets like…
- SSN
- Bank account numbers
- Phone Numbers
- Credit card numbers
- Birth Certificates
- License numbers
- Health Insurance numbers
- Download code
- Activation code “gaming”
- Claim numbers
- Serial numbers
- Love notes
- Addresses
Treat passwords like keys – No one is forced to remember the cut of their keys, they just need to keep track of them. If someone knew the cut of your house key, they could make a copy and get in your home. Why do we treat passwords any different?
What If The Attacker Downloads The Password Database?
What if the attacker was able to get the database of hashed passwords, wouldn’t SMS 2FA keep them from logging into the account?
I get this one a few times, but to that I say… does it matter how many locks are on your front door if the attacker got in through a window?
If we can assume they got the password database, why can’t we also assume they got the 2FA secrets or now control the 2FA? Or better yet, why do they need either if they’re already in the server?
But let’s assume they have gotten the hashed passwords and, for some reason, did not get to the 2FA.
We’re generating the passwords for the users! Comparing hashes from other leaks is pointless, and the hashes in our database are useless on other sites too.
With proper peppering or merely making the password long enough, the attacker having the password hashes is meaningless. As discussed earlier, guessing passwords takes forever and only worsens for the attacker when you use a slow hashing algo.
Don’t Forget Backup Codes
I’ve got to add the irony of backup codes.
Not every service that has SMS 2FA will do backup codes, but other 2FA do.
The irony of backup codes comes from the fact it’s a random code (password) that can turn the 2FA off.
If the weakest point of your 2FA comes down to a random password that the user did not create, then why not use random passwords from the start?
The best one comes from Google, which uses 8-digit codes. Yes, 8 numbers are what keeps someone from turning off your 2FA on your Google account. And they give you 10 of them!
It’s even funnier when you realize that many users have 2FA so they can keep using their bad passwords. After all, 2FA is treated as the “silver bullet to hacking“. So, in the end, what’s keeping an attacker out is 8 random numbers. I bet if you asked those users if they thought a password that was only 8 digits was secure, they would say no, after all, password requirements have trained them to think this way, yet that is what is protecting their account.
All roads lead to random passwords, but we’re stuck in a dogma that keeps us from using random passwords.
Is All 2FA Bad?
The problem is that we’re quick to jump to 2FA without fixing the user’s 1FA problem. We’re skipping over step one to get to step two without realizing the issues we’re actually trying to solve.
Not all 2FA is bad, but certain 2FA like SMS are not worth keeping when better solutions are available.
Some of what I talked about also affects TOTP 2FA, but that is for a different time. TOTP 2FA is better than SMS 2FA and use it if U2F is not an option. U2F would be the best 2FA, and I highly recommend it to anyone who wants 2FA. But I also understand U2F is not for everyone, so I push for generating passwords first.
Just whatever you do, don’t skip step one!


Recently exported all my password from Lastpass to bitwarden. Do you think I should change all my passwords since Lastpass once had access to them?
Depends on your threat level. For most people, it would not be necessary but I would at least change the passwords to the important accounts like email and banking.
makes sense. Thanks 🙂
ummm… I’m not sure I get your point. how does generating passwords prevent attacks such as the linked videos(specifically, Office365 and Lastpass)?
In both the attacks, the user puts in the code after typing the password(which could be whatever). Password being complex wouldn’t have stopped any of these attacks.
In that section, I point out that SMS 2FA doesn’t stop phishing attacks. What does stop phishing attacks is using a password manager as it won’t fill the password unless the URL is correct. So the user is better off in this case using a password manager with unique passwords than SMS 2FA. Even if the user did not use a password manager then SMS 2FA is still not offering any better protection so it’s not needed.