If you don’t trust password managers or fear “putting all your eggs in one basket” then the peppering method is for you.
Note: Peppering your passwords also have been called salting, secret salt, double-blind passwords, and password splitting but peppering is the more correct term so that is what we’ll use.
How To Pepper Your Passwords In Your Password Manager
When signing up for an account, use your password manager to generate a random password as shown below.
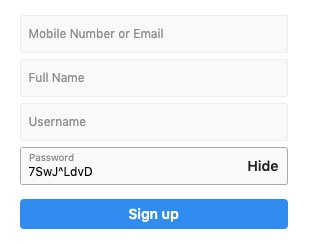
Before you press the sign-up button, add your pepper to the end of the password as shown below.
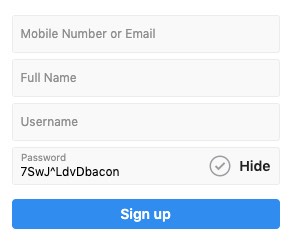
My pepper is “bacon.”
When you store the password in your password manager leave out the pepper as shown below.
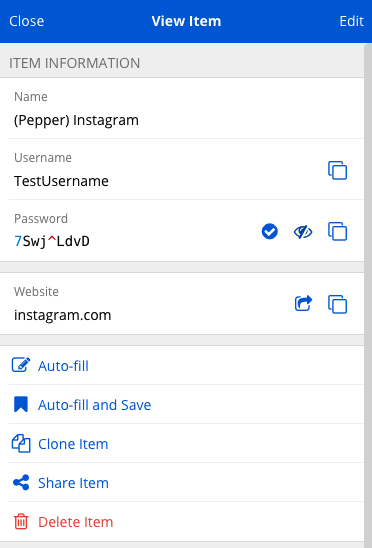
If you want you can add a reminder in the name field (Pepper) to remind you that you peppered that password.
When you go to log in to the website, have the password manager autofill the password it has and then add the pepper before pressing the login button.
If for some reason your password manager is breached the real password is not exposed.
Video How To:
Note: I used “salting” instead of pepper in this video but it’s the same thing.
What Pepper Can You Use?
You can pick a random word, a phrase, or a PIN number.
I recommend a PIN as it blends in well with randomly generated passwords. Example: Qwddjt68uKF2934 or Qwddjt68uKFPY57.
Make sure to be consistent, use only one pepper and at the same location.
What Passwords Should You Pepper?
Please do -not- pepper all your passwords!
Only pepper the most important passwords like the ones for your email or banking accounts.
Peppering all accounts will make your life harder then it needs to be.
Why Pepper Your Passwords?
I’ve found people have a hard time trusting password managers. They have a fear of the “all your eggs in one basket,” which is actually a good thing as explained here.
The real goal is to keep people from reusing passwords or using super weak ones. The only way I’ve found to do this is with a password manager, but this created new problems of trust. I feel the act of peppering your password solves the issue of trust with password managers that many people have.
With the peppering method, there is no excuse not to use a password manager.
Peppering vs. 2FA
Peppering is not meant to replace 2FA, but it does things that 2FA can’t.
Peppering is meant to protect your password manager vault from being completely compromised.
One way your password manager could be compromised is through phishing as this video shows.
As you can see, the victim had 2FA on their password manager but it did not save them from getting their vault items stolen. If they had peppered the important passwords the attacker would not have the whole password and thus the victim would have been better protected.
Here is a great break down of this attack.
Another way peppering protects your passwords is from the evil maid attack. If you have a roommate or someone that sneaks up to your open vault they would not have the full password and thus you’re better protected.
Peppering is also nice when a password manager doesn’t have the re-prompt for the master password on select vault items. Instead of waiting for your password manager to give you this feature you can have it now with peppering.
All 2FA, except for U2F, can’t protect you from phishing attacks. The best thing for protecting you from phishing attacks is your password manager. A password manager will not fill in the password unless the URL is correct. This is why I push people towards password managers more than 2FA and to protect their password manager I show them peppering.
I find people understand peppering better than teaching them TOTP 2FA, Push 2FA, or even U2F. peppering is also a relief to many as they have a fear of “keeping all their eggs in one basket”, without peppering many would not use a password manager and that is not what we want. We want to better secure people and scaring them away is not how we do it.
FAQ – Questions I Get About Peppering Passwords
What If I Forget My Pepper?
I suggest you write down your pepper and master password to your password manager and keep that somewhere safe. I go over why it’s crucial to write down your master password.
If you have someone you trust you can write down your pepper and master password and seal that in an envelope and give it to the person you trust. A safe deposit box works too.
Can I Use The Websites Name For The Pepper?
I would suggest you don’t because that is easy to figure out.
Does Peppering Protect Against Clipboard Snooping?
Yes, peppering could protect you against apps that snoop or look at your clipboard.
When Apple released its latest iOS update they made a change that alerted the user when an app looked at your clipboard. Since so many people copy and paste passwords on mobile this is a huge concern.
The great thing about peppering passwords is that when you copy it from the password manager, you’re only copying what the password manager has. Since the password lacks the pepper any app that snoops on your clipboard won’t know the full password.
To give you an example… say you’re logging into an app on your phone. So you copy the password but accidentally jump into the wrong app, and that app reads your clipboard and now has your password.
Or another example is you copied your password and logged in, then you move on to something else but your password manager did not clear the clipboard like it should, and your password remains, and any app you open after can now read the clipboard and get your password.
Since the password is peppered they would not have the whole password thus protecting you.
Is Peppering Secure?
One push back I get is if someone has gotten in your vault wouldn’t they also know your pepper?
No, unless you left the pepper in your password manager, there is no way the attacker knows your pepper. The attacker doesn’t know what they don’t know. All the attacker knows is that you must have changed that password and that is why it doesn’t work.
Security is about layers and peppering is just another layer. You’ll never have a perfect system but the more friction points you give to the attacker the better.
One of the great side effects of only peppering the important passwords is that the un-peppered ones act as honeypots. So if your vault is compromised the attacker will move on to the passwords that do work. Many websites send you an email letting you know of new devices logging in. So if you start to see a bunch of emails from different websites in your vault saying new devices are logging in then you know your password manager has been breached and it’s time to start changing the passwords and your master password.
What If My Peppered Password Ends Up In A Breach?
I only recommend you pepper the important passwords, this is your email and banking accounts. Those accounts becoming breached are very slim. Trust me, Google and most banks are doing hashing and protecting you better than the forum you only visited twice.
But there is still the possiblity.
The good news is that it doesn’t matter much as your passwords are still unique and randomly generated by the password manager. So knowing that you use “kr8DDFA8PxdYbacon” doesn’t help the attacker when the other password is “x7SKzeUHip7vbacon”.
If you want you can make your pepper look random. For example, “XBnXXAXueq3Pdjo4”, “djo4” is my pepper and it blends in better than a word. You could even do your initials and a number, so mine would be “tf57”. Easy to remember and it doesn’t stand out. A lot of people use a PIN number which doesn’t stand out either.
I would not stress about it, use whatever pepper you want. You’re already doing better than most by using a password manager and peppering.
Password Salting vs. Password Peppering
This technique has been called many names such as salting, secret salt, split passwords, partial passwords, double-blind passwords, and so on.
Of all the names, salting and peppering are the more correct terms with peppering being the more correct term of the two.
Both salting and peppering is a method of adding something to the end of a password. What makes them different is that the salt is not meant to be secret and is often stored alongside the password in a database. A “secret salt” or, more commonly known, a pepper, is not stored anywhere near the password and is meant to be hidden.
This concept of salting or peppering passwords in a password manager is not new either, here are examples 1 – 2 – 3 – 4 – 5 – 6 – 7.

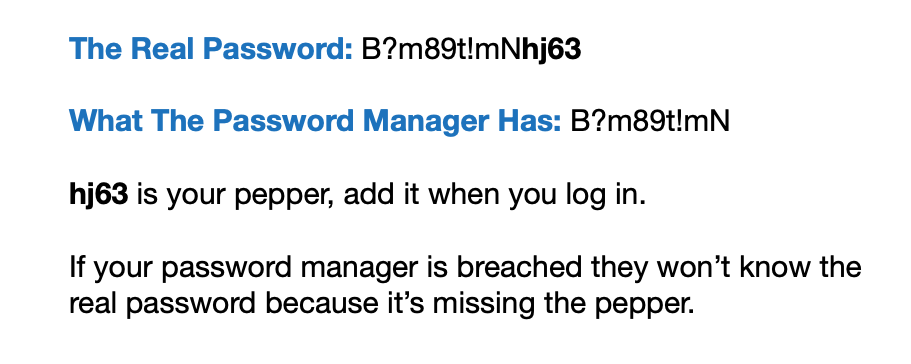
This is a very good article. Thank you!
THANKS A TON! This information is sooo valuable. I finally get to feel a little more secure about my financial accounts not being compromised now!