There has always been a hot topic of getting rid of SMS 2FA because of its insecurities. NIST was going to drop it from its recommendation but backed out after much controversy.
Now in 2020, a Princeton University study has come out demonstrating how bad SMS 2FA can be exploited. They even went as far as to make a website called “IsSMS2FASecure.com” and placed a giant NO at the top to express how they feel.
To me, this whole debate over SMS 2FA is an interesting one, as I can see the point from both sides.
I’ve yet to see anyone break it all down and show how each side is correct. That is what I’m attempting to do in this article and ultimately figure out if SMS 2FA is worth it or not.
What Is SMS 2FA?
To describe SMS 2FA, we must understand 2FA. 2FA is two-factor authentication. The factors are something you know, something you have, and something you are.
The more factors you supply, the more proof you have of the right user.
These factors can be passwords (something you know) or a code sent to your phone (something you have) or a fingerprint (something you are). Since a lot of people have a phone, it makes having SMS 2FA (text message-based 2FA) the easiest to implement.
When you have 2 factors (password + text message), it’s obviously better than only having 1 factor (only password). No sane person can argue against this.
From the research I’ve done, this is often the full stop for most people who believe it’s better to have 2FA than nothing at all. On this fundamental level, they’re right, but in reality, there is more to it.
The Problem With SMS 2FA
As the Princeton Study showed us, it was not hard for them to SIM Swap their test phones.
A SIM Swap is when you call the phone carrier and tell them you lost your phone and need to change to another one. The study demonstrated that you only have to answer basic questions, and the number was ported to someone else, the attacker.
When the attacker gets access to the phone number, they can do two things.
If the attacker knows the password, they can combine it with the second factor of the phone number they just ported and log in.
The other way is resetting the password through an SMS password reset and thus gain access to the account. The study showed us several websites that allowed you to bypass the password and gain access to the account just by having the user’s phone number. We’ve also seen this in the real world with users losing money, especially from cryptocurrency exchanges.
SMS 2FA and SMS Password Resets Are Not the Same!
Many experts don’t want to clump SMS password reset in with SMS 2FA.
Once again, they’re right – they’re not the same.
While they’re not the same, it would be disingenuous to say they don’t often run together. Most of the time, they’re grouped with each other without the users knowing and leading them to a false sense of security. This false sense of security was pointed out in the Princeton University study (Page 9, number 4).
This is one of those grey areas where both sides are correct.
SMS 2FA is not the same as SMS Resets. But in the real world, we see far too many sites that have SMS 2FA also have SMS Resets because they already have the user’s phone number. You wouldn’t have SMS Resets if the SMS 2FA didn’t lay the groundwork to get the phone number.
And it’s true that some services have SMS 2FA but don’t allow SMS Resets. While this is how it should be done, the problem is that we don’t know if in the future they’ll add SMS Resets.
If the site does roll out SMS reset, will they first warn their users about it? Has any website in the past rolled out SMS reset and notified its users? I can’t find any.
This uncertainty is very worrying.
SMS 2FA Is Not Perfect, But We Should Still Use It
Every infosec expert knows SMS 2FA is not perfect, but we should still use it.
Like many times before, the experts are right.
The rationale is that someone targeting you and porting your number is small. There are much easier targets out there, so it’s better to use SMS 2FA then nothing at all.
With the ever-changing internet, is this statement still holding true in today’s world?
Real-World Examples
What is the most interesting part of the SMS 2FA debate is seeing how it affects real people.
We’re seeing countless examples of people losing money or their accounts due to the weakness in SMS.
While celebrities and the rich getting hacked make the news it’s the average user that we need to watch out for. If the average user is getting hacked it’s a trickle-up effect for everyone else.
I stumbled upon a great example from an average user recently on Reddit. The original poster(OP) was warning people that SMS 2FA is not safe, and you should not use it. Then one of the comments made the same argument that many of the experts make – you should still use SMS 2FA because it adds another barrier, and the attacker will just move on to someone easier to target. OP thought the same thing too, but yet he was still hacked and lost money.
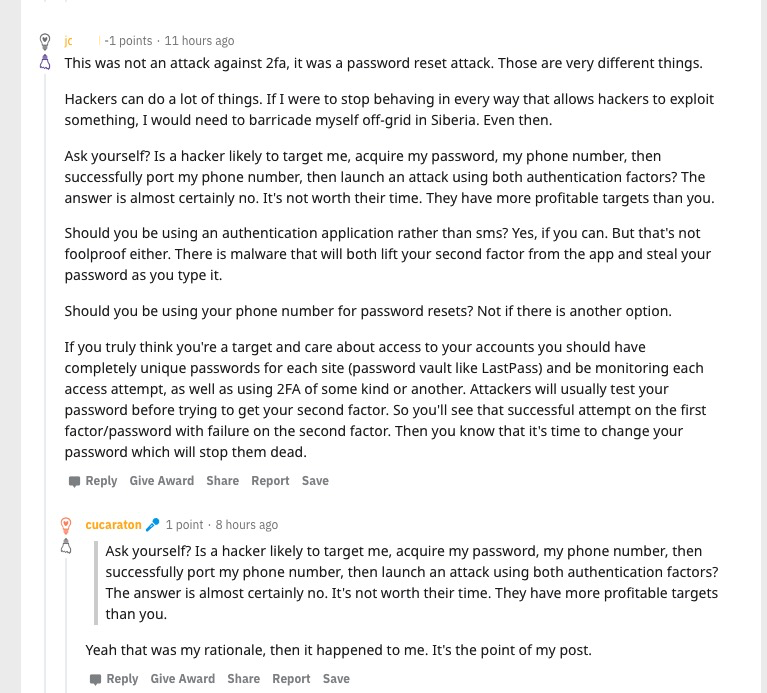
Another real-world example. Link – Archive – Image
Here are just a few more examples of people losing their accounts due to the weakness of SMS.
- https://www.vice.com/en/article/y3g8wb/hacker-got-my-texts-16-dollars-sakari-netnumber
- https://www.theverge.com/2017/9/18/16328172/sms-two-factor-authentication-hack-password-bitcoin
- https://www.kaspersky.com/blog/ss7-hacked/25529/
- https://nakedsecurity.sophos.com/2019/10/11/hackers-bypassing-some-types-of-2fa-security-fbi-warns/
- https://www.pcmag.com/news/reddit-hacked-despite-sms-two-factor-authentication
- https://www.intercede.com/us/cyber-criminals-hack-uk-based-bank-using-sms-two-factor-authentication-vulnerability-how-it-could-have-been-prevented/
- https://thenextweb.com/hardfork/2019/01/17/bitcoin-att-sim-swapping-victim/
- https://www.darkreading.com/endpoint/i-hacked-my-accounts-using-my-mobile-number-heres-what-i-learned/a/d-id/1336315
That last link was from Nicole Sette, who is a director at a cyber-risk investigations company and a former FBI cyber analyst. Her article and the lessons she learned have me questioning SMS 2FA.
We have real people and real experts showing us the flaws with SMS 2FA and it’s brother SMS Resets.
This should make everyone pause and want to reexamine SMS anything when it comes to security.
Something I’ve Noticed
It’s funny when you have this debate in the cryptocurrency circles. All of them will say you should never use SMS 2FA and should use app-based 2FA at the minimum.
They have this fear for a good reason; a lot of the SIM Swap attacks have been on people who held cryptocurrencies.
It’s uncertain if Bitcoin or any cryptocurrencies will take over, but what is certain is more and more people will be doing online banking in the future.
With most banks using only SMS 2FA, it makes you wonder why they haven’t dropped it for something better? Of all the businesses that for sure need to get rid of SMS 2FA and replaced with something better, it would be the banks.
Sure, as Troy Hunt has pointed out, banks do a lot more than just that to protect us, but it’s still worth questioning it.
Why Keep Using SMS 2FA?
The goal is to minimize risk the best we can because we can never entirely remove it.
Yes, there have been average everyday users who have lost accounts or money due to the insecurities of SMS but should we do away with SMS 2FA?
No.
But this brings up a good question…
What is an acceptable percentage of account takeovers before we outright ban the use of SMS anything as a factor?
What we want is ZERO accounts being stolen due to SMS, but is that even possible? Not unless you get rid of SMS as a factor.
We shouldn’t get rid of it because having 2 factors is better than 1. This saying gets thrown around a lot, but why do we say it… why do we have SMS 2FA in the first place?
Why Do We Have SMS 2FA?
As stated before, having 2 factors is better than 1.
If your first factor is already known, the second factor will save you.
How would the first factor, your password, be already known?
There are several ways, but the biggest is from password reuse.
A website you used in the past got breached, and the passwords were stolen. The hackers use bots to see what other accounts you used that password on so they can steal those too. This is called a credential stuffing attack.
A credential stuffing attack is the biggest threat to users then any other attack we have today. Phishing, malware, and other attacks exist but not at this level. I’ll talk more about these other attacks at the bottom.
Our money is on credential stuffing. Here’s some back-of-the-envelope math:
— Shape Security (@ShapeSecurity) January 22, 2020
4B internet users globally
1B credential stuffing attacks per day
50% of all internet users have had a set of credentials compromised, which are then being used in an attack every other day.
People are bad with passwords; it’s no secret (unlike their passwords lol).
It’s just a fact of life that users will pick bad/reused passwords, and adding 2FA fixes this problem.
Since most users have a phone number, SMS 2FA has become the most popular form of 2FA.
This leads us to a new problem.
2FA Is Not an Excuse for Bad Passwords
The whole reason we have 2FA is that 2 factors are better than 1.
But if the first factor is already known or easy to guess, you don’t have 2FA anymore – You have 1FA.
Each factor is meant to be a friction point, just like having to enter two locked doors. If you keep the key in one of the locked doors, you’re defeating the whole point.
Implementing SMS 2FA because your users use bad passwords puts you back at 1FA. You’ve defeated the whole point of having 2FA.
If we’re going to end up with 1FA, why not use the best option for 1FA, a randomly generated password? A randomly generated password that you only use on one website is the best 1FA you can have.
Sure, there are other ways your password could be stolen, but security is not 100%. We tackle the bigger threats first to better protect the mass.
Right now, the biggest threat to users is password reuse, and websites are using the most prominent form of 2FA, SMS 2FA, to tackle this problem. This is not solving the problem, it’s making it more sticky.
It’s A Sticky Situation
After boiling it down, we understand why we have SMS 2FA is because users are bad with passwords. If users are reusing passwords, you don’t have 2FA anymore but 1FA. But you need the second factor because users are reusing passwords.
You end up with a sticky situation.
What can we do?
What I’m Going To Do
I’m not going to tell you what to do, but I’ll let you know what I’m doing.
If we’re using SMS 2FA as a way to fix the password reuse problem, then we don’t have 2FA anymore but 1FA.
If I’m stuck with 1FA, I’m going to use the best 1FA possible, which is a randomly generated password that I only use for that one website.
While my 1FA will be solid, I feel having SMS 2FA is like playing the lottery. Yes, it will make my account more secure, but that goes out the window if the site allows you to reset your password via SMS. Not only that, but if the site doesn’t allow SMS reset, is there a chance they’ll add it in the future, and if they do, will they even warn me?
Sometimes to win the lottery, it’s best not to play it.
For me personally, I’m going to be using a random password for all accounts. If the site offers SMS 2FA, I’m going to avoid it if I can. If the site provides something better than SMS 2FA like an app-based or Yubikey option, I’ll go with that. If Email 2FA is an option I’ll go with that over SMS 2FA because I can secure my email with proper 2FA like app-based or Yubikey.
For me, SMS 2FA is not worth the hassle. Most people are not going to check the password reset flow to make sure the site is doing it right. And I’m very confident no one is going to continually check to make sure the site doesn’t add SMS reset in the future.
We know that phone carriers won’t do anything about this issue either. They’re in a cut-throat business, and the slightest unhappy customer will jump ship to someone else. Making it easy for a customer is more important than their security.
What About Phishing, Malware, and Other Ways To Steal Passwords?
Your password being stolen from another website and used to see what other accounts they can log into is the biggest threat the average user is facing.
If you’re a celebrity or high profile person, this changes more to phishing and malware.
It would not be fair of me not to include these other attacks when talking about someone stealing your passwords.
Once again, I’m not going to tell you what to do, but I’ll tell you what I’m doing about these particular attacks.
I feel that using a random password unique to each website is the best option instead of having SMS 2FA. If the service allows for app-based 2FA or Yubikeys, then I’ll for sure use those instead of SMS 2FA.
To manage these passwords, the best thing to do is to use a password manager for two good reasons. The first is for managing all these passwords, and the second is to help stop phishing attacks.
The great thing about a password manager is that it won’t fill in the password unless it’s the correct URL. While “google.com” and “googIe.com” look the same to us, it can’t trick a password manager.
For malware, the best answer is always going to be to run anti-virus or anti-malware software on your computer. Yes, this may mean you need to run something better than Windows Defender.
In a way, the password manager can also help solve the malware problem too. I’ve discussed several ways to protect your vault by either peppering your important passwords or using the two password manager method. While these methods are not foolproof it’s still better than what most people do.
Don’t forget the first rule of the “10 Immutable Laws of Security”…
In other words, if your computer is infected there is not much you can do about it no matter if you use a password manager or not. It’s best to try to keep it from getting infected in the first place so use antivirus.
TL;DR
The lottery of SMS 2FA is excellent for some; the odds are in their favor. For how long I don’t know, but I do know it’s better to move away to something better sooner than later.
Update
A solution to the SMS 2FA problem might be unfolding before our eyes with the use of encrypted messaging like Signal and WhatsApp.
A lot of the encrypted messaging apps don’t need a phone number but instead, use a username. If more people start using these apps the industry will have to move to sending messages through these apps or use another option.
The SMS itself might be dying off and being replaced because people are pushing for privacy. It will be interesting to see where this goes in the future.