Storing your 2FA TOTP tokens in your password manager has become a hotly debated topic.
In a perfect world, you should NOT keep your 2FA tokens in your password manager.
But we don’t live in that world, and the honest answer is a lot more nuanced. And for most people, keeping your 2FA tokens in your password manager is fine.
What Is 2FA (Two-Factor Authentication)?
- Your password = 1st factor.
- Something you have = 2nd factor.
The something you have can be your phone. The most popular 2FA is the one you get by SMS. Another more secure version is app-based or also called TOTP.
TOTP = time-based one time passwords.
When you set up TOTP 2FA, you scan a QR code using an app like Authy or Google Authenticator. The app gets a shared secret out of the QR code and combines it with the current time to create a 6 digit code that changes every 30 seconds.
Instead of storing the tokens in Authy or Google Authenticator, many password managers allow you to save them and will also generate the code too.
Why Storing 2FA Tokens In The Same Place As Your Passwords Is Bad?
The reason you have 2FA is if your 1FA, your password, is already known.
If you keep your passwords with your 2FA and the attacker got to your passwords, they would also have your 2FA, and the 2FA would not be helpful anymore.
If you boil it down to this simplest form, you would be correct not to store your 2FA in your password manager.
… but it’s not that cut-and-dry.
Why Storing 2FA Tokens In Your Password Manager Is Not That Bad?
There are 4 main reasons why storing your 2FA inside your password manager is fine.
1. Timeliness
TOTP codes are based on time and change every 30 seconds, unlike your static password.
The code changing can be beneficial if you’re in a situation where you have an attacker “in the middle” listening.
The attacker may have your password, but the 2FA code they also gathered is expiring soon. This timeliness can be super helpful in fighting certain attacks.
1Password did a great write-up about this timeliness here.
2. Redundancy
If you use a password manager and give every account a unique password, at worst, having TOTP 2FA is redundant security.
Redundancy is not a bad thing, especially when it comes to security.
As talked about in our article about what makes Google Authenticator and other TOTP apps so special is the shared secret.
The shared secret is nothing more than a randomly generated password.
The truth when it comes to Google Authenticator, Authy, or any TOTP app is that it’s just another password manager. The difference is that the password is combined with the current time to create a 6 digit code that changes every 30 seconds.
What really will blow your mind is that many of these TOTP apps don’t encrypt the secrets when stored on your phone. But, if stored in an actual password manager, 2FA tokens would be encrypted with all your passwords. So one could argue that keeping your 2FA tokens in your encrypted password manager would be a security upgrade compared to many TOTP apps.
3. It’s Already On The Same Phone
You shouldn’t store your 2FA in the same place as your passwords.
But most do this anyway without realizing it when they keep their 2FA app on the same phone that holds their password manager.
For it to be real 2FA, you need to keep your 2FA on a different device than your password manager. Unless you have 2 phones or a security key, this gets tricky fast.
The irony is that the people who are against keeping 2FA tokens in an encrypted password manager are okay with keeping them on the same phone un-encrypted. The real kicker is that the most popular TOTP 2FA app, Google Authenticator, doesn’t even offer PIN or fingerprint unlock – anyone using your phone can open the app and read the codes.
4. Peppering
The most substantial reason why it’s fine to store 2FA codes in your password manager is Peppering.
Learn more about Peppering your passwords here.
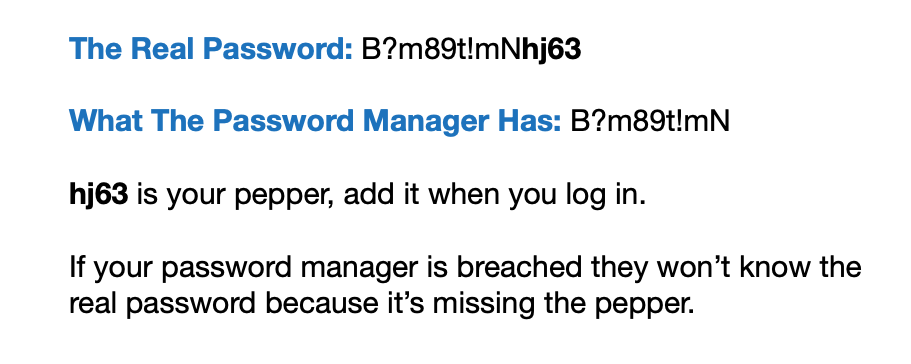
If you pepper the password to the accounts that also have the 2FA stored, you’ve effectively beat the system.
You can have your cake and eat it too!
You’re not storing the full password with the 2FA, so someone getting in your password manager won’t have everything.
Sometimes You Got To Have 2FA
Sometimes you just got to have 2FA for an account.
It could be your boss, IT, friends, family, or whatever requiring you to have 2FA.
If you’re forced to have 2FA keeping it in your password manager becomes super convenient.
Many password managers like Bitwarden or 1Password will either fill the 2FA code for you after the password or copy it to the clipboard so you can paste it. Once you experience this, it’s like magic and makes logging in so much easier.
Other Reasons Why Having 2FA In Your Password Manager Is Fine
The biggest reason to keep your 2FA tokens in your password manager is that it’s in one location and gets backed up.
Far too many people don’t realize that apps like Google Authenticator and many others don’t automatically backup your 2FA tokens. So if you get a new phone or lose your phone, you also lose your 2FA.
Storing the tokens in your password manager also gives you more flexibility if you want to get out. Many of these TOTP apps don’t allow you to get the secret out once it’s saved.
Plus, it’s easier to secure one thing to the max than worry about the security of multiple little things.
Have 2FA On Your Password Manager Account
If you’re going to store 2FA tokens in your password manager, you should at least have 2FA on your password manager account.
So if someone wanted to get in your password manager to steal your passwords and 2FA, they would also need to get around the 2FA on your password manager account. An app like Authy or a security key like a Yubikey is a great option for your password manager account.
Don’t forget to store your password manager recovery codes somewhere safe. Don’t store them in your password manager, as you’ll lock yourself out. It’s best to keep them with your master password in a safe location in your home.
Security Is About Trade-Offs
There will never be a perfect system, so you must consider what works best for you.
For the average person, storing your 2FA in your password manager is fine. But, shoot, simply using a password manager and giving every account a unique password already puts you light years ahead of most, and adding 2FA to that is just the cherry on top.
But if your threat level is not the same as the average person, you may need to change things.
Just don’t let your paranoia get the best of you.

Very interesting article. I think by saving your 2FA keys in your password manager, you still have 90% of the security 2FA gives you. It will only put you in danger if someone gains access to your password manager’s vault. But let’s be honest, that’s the least possible way someone might steal your passwords. It protects you the same in all other types of attacks.
I would use Bitwarden as an authenticator if I could just delete my authenticator app (Aegis authenticator), but I still need it for Bitwarden, so I just keep using it for everything.