What if your password manager gets hacked? What if you get run over by a bus? What if you get struck by lighting?
Life is full of “what if’s” but that doesn’t mean we should stop living. Just because there is a chance you’ll get killed in a car accident doesn’t mean you should never drive. There are steps you take like wearing a seat belt that put the odds in your favor.
The same thinking goes for password managers. Just because there is a chance someone somehow could get in doesn’t mean you should not use one. You must put on your “seat belt” with a password manager to better your odds because the alternative of password reuse (walking) is not worth it.
The car analogy is probably not the best because getting your password manager breached is far less likely but it does help demonstrate the idea.
Try Peppering Your Passwords!
When I have someone who is afraid to use a password manager I show them the peppering your passwords method. This method is so smart that I rarely have someone not give a password manager a shot after learning about it.
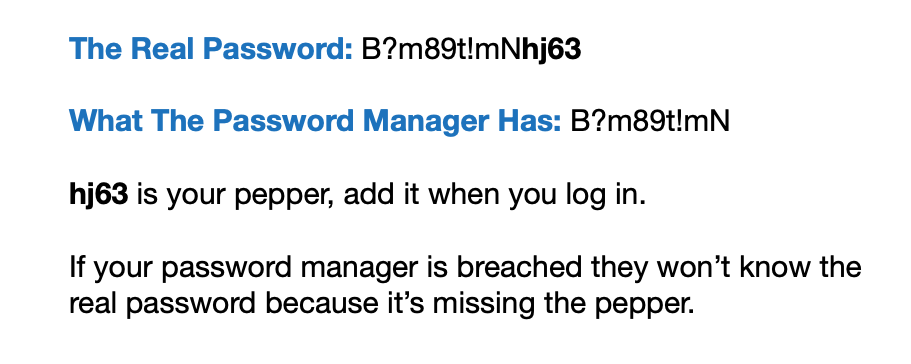
Peppering your passwords removes the fear that many people have when it comes to password managers. I wouldn’t pepper every password only the important ones like email and banking.
A Misunderstanding
The fear people have over password managers is from a misunderstanding of how they work. Movies portray hackers getting in with a few keystrokes and destroying everything.
Life is not like the movies.
The way password managers work is by encrypting your entire passwords in a vault. To decrypt this vault, you need the master password, the one password that rules them all.
Then the question of, “what if they crack my master password” comes up.
To answer that question depends on how strong your master password is and what encryption is being used on your password manager.
Why Cracking Your Master Password Is Hard
Despite what the movies say and what many people think, cracking a password is not an easy task.
I wrote an entire post on how long should your password be https://passwordbits.com/password-how-long/
In that
- 9 Character long password would take 67 minutes to guess all possibilities.
- 10 Character long password would take 3.27 days.
- 11 Characters would take 229 days.
- 12 Characters, 44 years.
As you can see, adding just one more character to our password makes it exponentially stronger. And this is with a computer so fast that it might not even exist. Your home computer would be nowhere near these numbers.
It gets to a point where if your master password is at least 15 characters long then you’re fine from pure brute-force guessing.
How To Come Up With A Mater Password
Coming up with a good master password is easy to do, this guide will show you how.
When it comes to master passwords, it’s best to keep it simple but strong, and that is what we do in that post.
Password Manager Strength
Beyond having a strong master password, the password manager also helps to keep your account secure. Most, if not all, strengthen your password.
They use what is called “Key Expansion Algorithm.” In simple terms, it’s like taking a number X and multiplying by another number Y so many times. Where the number X is your plain master password.
Depending on what algo they use the number of times they perform the math can vary. Some
They do this because it requires time to calculate each guess. If it takes 1 second to calculate one guess, this greatly slows down a brute force attack. If you ever wondered why when you log in to your computer or password manager, and it seems to hang for a second, this is the reason why. This slowing down is used in many places to stop brute force guessing of passwords.
But The Eggs In One Basket!
The “keeping your eggs in one basket” gets thrown around a lot when password managers are mentioned. Let me start by answering that with this question.
What do you trust more…
- Your passwords in one secure location you control or
- Reusing passwords that are stored on hundreds if not thousands of other people’s computers.
If you’re not using a password manager, then you’re more likely to reuse passwords. Then that password is only as good as the security of the server it’s stored on. With so many websites still storing passwords in plain text or using a weak hashing algorithm do you really want to run the risk?
All it takes is one site you signed up for to get breached or even worse their 3rd party partner who they shared their data with to get breached. It happens more than you think. Now that password is known, and since so many people reuse passwords it will get tried on many other websites, this is call credential stuffing. Now you’re screwed and have to clean up this mess and remember all the sites you used that password on.
If you used a password manager, you could have given every account a unique password. If one of those sites gets breached no big deal as the password was not used anywhere else. All the rest of your passwords are stored securely in your password manager.
The hand full of you who say you give every account a unique password because of some algo you created I have a post just for you.
And yes, I hear you…
What If The Password Manager Company Gets Breached?!?!
A central location full of people’s passwords sure does seem like the perfect thing to hack. Its been done to companies before, example.
This is where it’s important to understand how each company stores your data. Some do it better than others, and some are just lazy. Just like buying a car it’s important to look at their safety
The way most password managers work is that they’ll store your database of passwords, but they won’t save the key.
If they don’t have the key, no one can open the vault.
How do you know they don’t have the key? They tell you if you lose your master password they can’t reset it. This is why you must not forget your master password, write it down and put in a safe if you have to.
Since they don’t store the key and use “Key Expansion Algorithms” it’s not worth the time or effort especially if they use a secret key to further make your master password stronger.
The data that they can take from a breach of a password manager server is useless unless they have the key. To get the key and figure out all the little nuances of how the data is stored and who the information belongs to is not worth the time and effort. It’s not like these password manager companies are storing passwords in a bucket for anyone to dump their hands in. They plan for these things to happen as their business depends on it.
It honestly would be easier to go after low hanging fruit of people who reuse passwords or phish it from them. Another great thing about password managers is that they help fight phishing attacks, the plugins they use won’t fill in the login details unless the URL matches 100% correctly.
This whole argument gets thrown out if you don’t use a cloud-based password manager like KeePassXC. Your vault is kept local so to get to it you need to be local too. Even if you stored it in your Dropbox account, it’s still far more secure then someone else’s server full of passwords.
The issue with local password managers is that you must manage them and back them up yourself. This is a trade-off many people are willing to make.
This brings me to my next point and something you should consider doing.
Important vs. Non-Important
When it comes to passwords, it’s easy to separate our important passwords from the not so important ones.
I bring this up to help the people who are worried about keeping all your eggs in one basket. You can have multiple baskets – strong secure baskets.
There is no rule saying you need to use only one password manager or you can’t have multiple vaults.
With a password manager like KeePassXC, you can have as many vaults as you want. Don’t go overboard with the idea; two should be fine because the more you have, the more master passwords you need to remember.
You can have one vault for your important passwords like banking and email accounts. The other vault could be for boring everyday passwords like twitter or that one forum you go to all the time.
I talk more about the 2 password manager method here.
Note: This idea is so good that even Tom’s Guide wrote about it. Very similar to my idea where you use 2 password managers, one for important accounts and one for non-important accounts.
Other Options to the Two Password Manager Idea
Another option is to have one vault or one password manager to hold everything and let the web browser store a second copy of the unimportant passwords. Never save the banking or other important passwords in your web browser’s password keeper.
If you want to take it to the extreme, you could even store the critical passwords on paper that you keep in a safe. Just make sure all passwords are unique.
If you think about it how often are you using your Google password or banking password? Once Google has you logged into a certain computer, they keep you logged in for what feels like forever. With banking apps becoming easier to use then a website and your smartphone being more locked down and secure than your PC it only makes sense to do banking on your phone.
I know many of you exist where you do have to log in to that one email account almost every day. For you, a solution would be to keep just the password to that account in your everyday non-important password manager. I bet you know the username because its an email that you use all the time and all you need is the password. If for some reason your password manager gets breached you have only the password and not the username or even the URL stored.
You don’t have to use just KeePassXC for both options. You could use something like Bitwarden for your non-important logins and a KeePassXC vault for important stuff or write them down. There are many possibilities to pick from and no wrong way about it. Do whatever fits your needs.